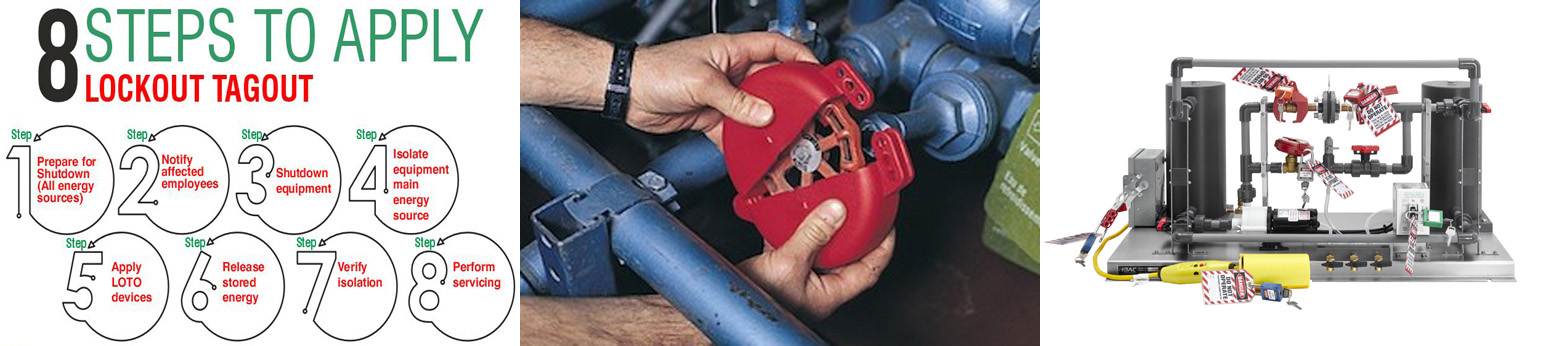
Procedures, Devices, Training, and Audits Done Right

Lockout/tagout (LOTO) remains one of the most critical and most frequently misunderstood elements of a manufacturing safety program. Many facilities believe they “have LOTO” because they own locks or have a binder of procedures on file. An effective lockout/tagout program is a system, not a document.
At PowerSafe Automation, we regularly encounter facilities with good intentions but fragmented execution: generic procedures, mismatched devices, inconsistent training, and audits performed only to satisfy a checkbox. These gaps create real exposure — not just to OSHA citations, but to serious injury, downtime, and liability.
If you are building or rebuilding a lockout/tagout program, there are four foundational pillars you must address together:
- Machine-specific LOTO procedures
- Properly selected lockout/tagout devices
- Role-based employee training
- Ongoing audits and program verification
Missing any one of these weakens the entire system.
Why Lockout/Tagout Programs Commonly Fail
Before diving into best practices, it is important to understand where most programs break down.
Common failure points we see include:
- One procedure applied across multiple machines
- Energy sources not fully identified (stored, secondary, or gravity)
- Lockout devices that do not physically prevent re-energization
- Training that lacks machine-specific context
- Annual audits performed without observation
From a regulatory standpoint, intent does not matter. Programs are evaluated based on whether hazardous energy is effectively controlled every time servicing or maintenance occurs.
1. Lockout/Tagout Procedures Must Be Machine-Specific
A compliant and usable lockout/tagout program starts with accurate, machine-specific procedures.
What a Compliant Procedure Must Include
Under OSHA 29 CFR 1910.147, each procedure must clearly document:
- All hazardous energy sources (electrical, pneumatic, hydraulic, mechanical, thermal, gravity)
- Exact energy-isolation points
- Proper shutdown sequence
- Lockout device application steps
- Verification of zero-energy state
- Safe restart process
Common Procedure Gaps
- Generic templates reused across equipment
- Missing secondary or stored energy sources
- Procedures written without maintenance input
- No photos or diagrams of isolation points
PowerSafe Best Practice
Effective procedures are:
- Developed at the machine — not from drawings alone
- Verified with maintenance and engineering personnel
- Illustrated with photos or schematics
- Written in clear, task-based language
A simple test: Could a newly authorized employee safely lock out this machine using only the procedure?
2. Lockout/Tagout Devices Must Match the Hazard

Owning lockout devices does not guarantee energy control. Devices must be correctly selected, applied, and standardized.
Device Selection Matters
Each energy-isolating device must be:
- Capable of being locked in the OFF or safe position
- Durable for the environment
- Clearly identifiable and dedicated to lockout use
Common device categories include:
- Electrical disconnect lockouts
- Valve lockouts (ball, gate, butterfly)
- Pneumatic and hydraulic lockouts
- Group lockout hasps and boxes
Device-Related Risks We See
- Tags used without locks when locks are feasible
- Locks that can be bypassed or removed without tools
- Inconsistent lock colors or personal identification
- No defined group lockout process
PowerSafe Best Practice
A robust LOTO program includes:
- Standardized locks and tags
- Clearly defined personal lock ownership
- Group lockout procedures for multi-person tasks
- Device selection verified during procedure development
3. Lockout/Tagout Training Must Be Role-Based
Training is not about awareness alone — it is about authorization, competency, and accountability.
Employee Categories Matter
A compliant program distinguishes between:
- Authorized employees – perform lockout/tagout
- Affected employees – operate or work near locked-out equipment
- Other employees – present in the area
Each group requires different training content and depth.
Training Gaps That Create Risk
- Same training delivered to all employees
- No documentation of authorized personnel
- No hands-on, machine-specific instruction
- No retraining after equipment changes or incidents
PowerSafe Best Practice
Effective LOTO training includes:
- Classroom and hands-on components
- Machine-specific examples tied to procedures
- Clear authorization records
- Defined retraining triggers
If an employee applies a lock, they must fully understand the energy they are controlling and the consequences of failure.
4. Lockout/Tagout Audits Are a Requirement — Not a Formality
Annual lockout/tagout audits are one of the most overlooked — and most cited — requirements.
What a LOTO Audit Actually Involves
A proper audit includes:
- Reviewing each machine-specific procedure
- Observing authorized employees performing lockout
- Interviewing employees with their understanding
- Documenting deficiencies and corrective actions
A LOTO audit is not:
- A desk review
- A sign-off without observation
- A one-time exercise
Audit Best Practices
High-performing facilities use audits to:
- Validate procedure accuracy
- Confirm training effectiveness
- Identify drift in real-world execution
- Demonstrate due diligence and continuous improvement
How Lockout/Tagout Fits Into a Broader Safety Strategy
Lockout/tagout should not exist in isolation. The strongest programs integrate LOTO with:
- Machine risk assessments
- Safeguarding and interlock design
- Maintenance standard work
- Engineering documentation
- Overall safety culture initiatives
At PowerSafe Automation, we view lockout/tagout as a critical control layer within a larger machine-safety and risk-reduction strategy — not just a compliance requirement.
Build a System — Not a Binder
A lockout/tagout program only works if it functions on the shop floor, under real conditions, with real people.
When building or improving your program, focus on:
- Accurate, machine-specific procedures
- Proper devices that physically control energy
- Meaningful, role-based training
- Regular, documented audits
If one element is weak, the entire system is compromised.